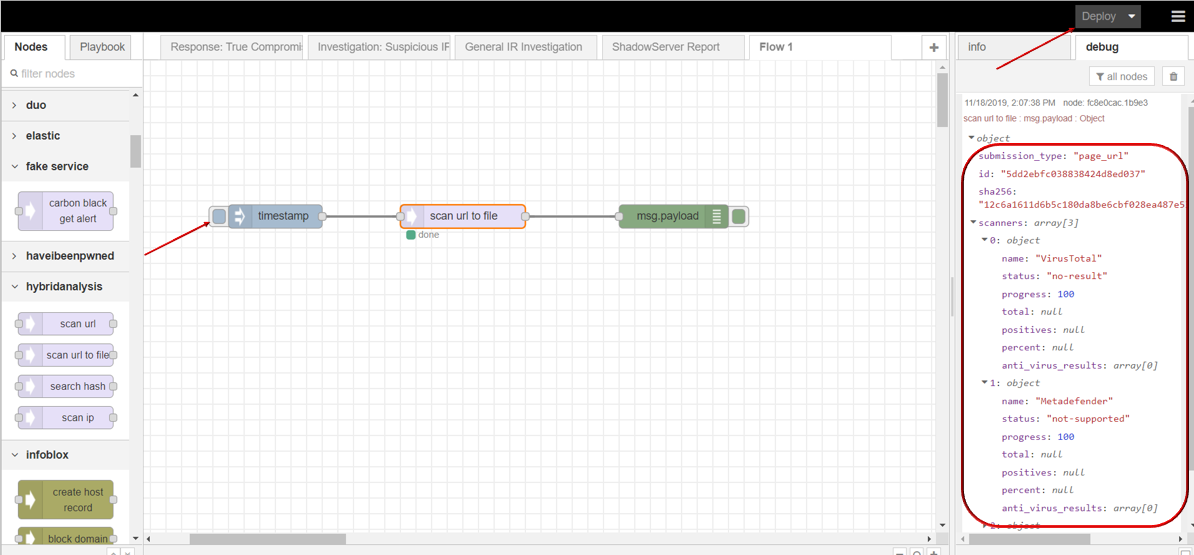
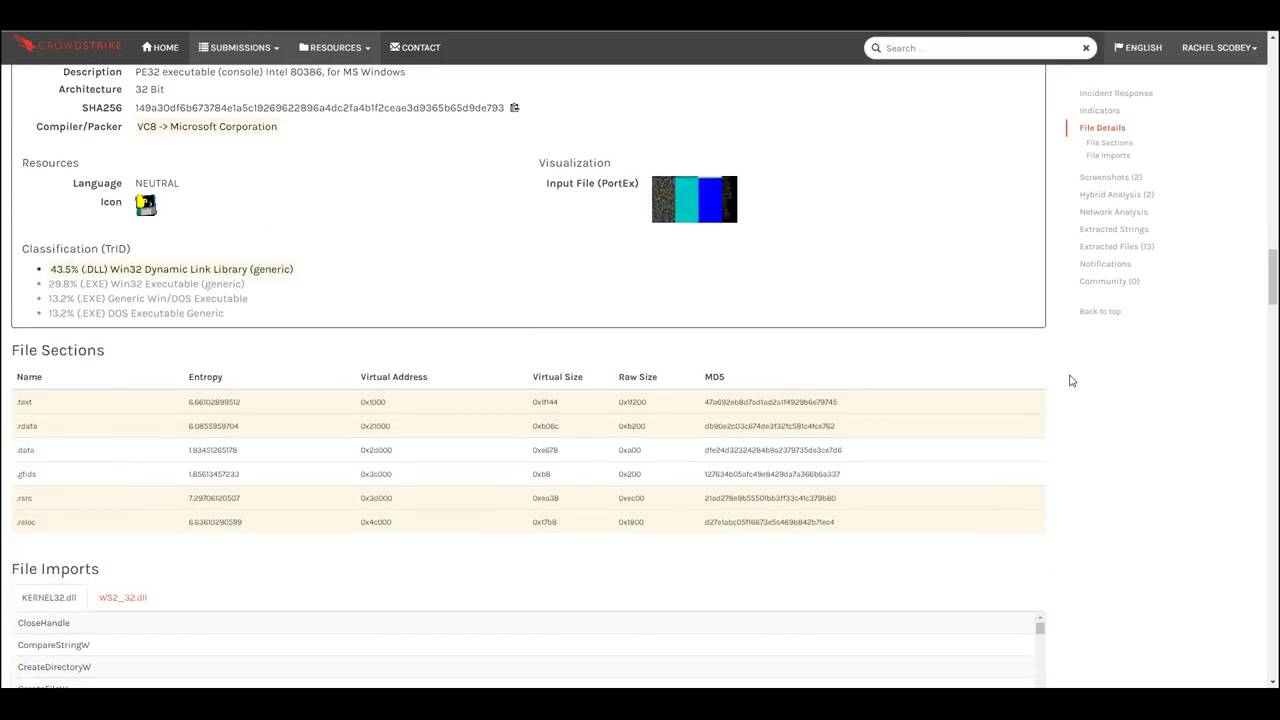
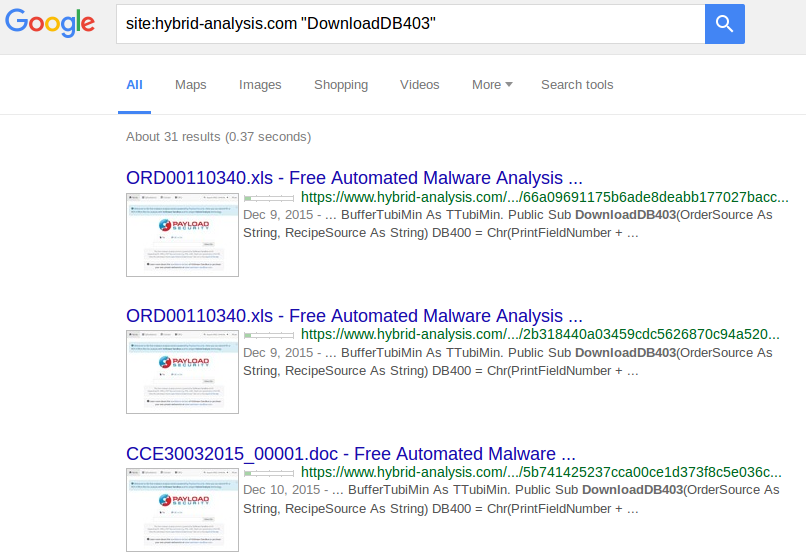
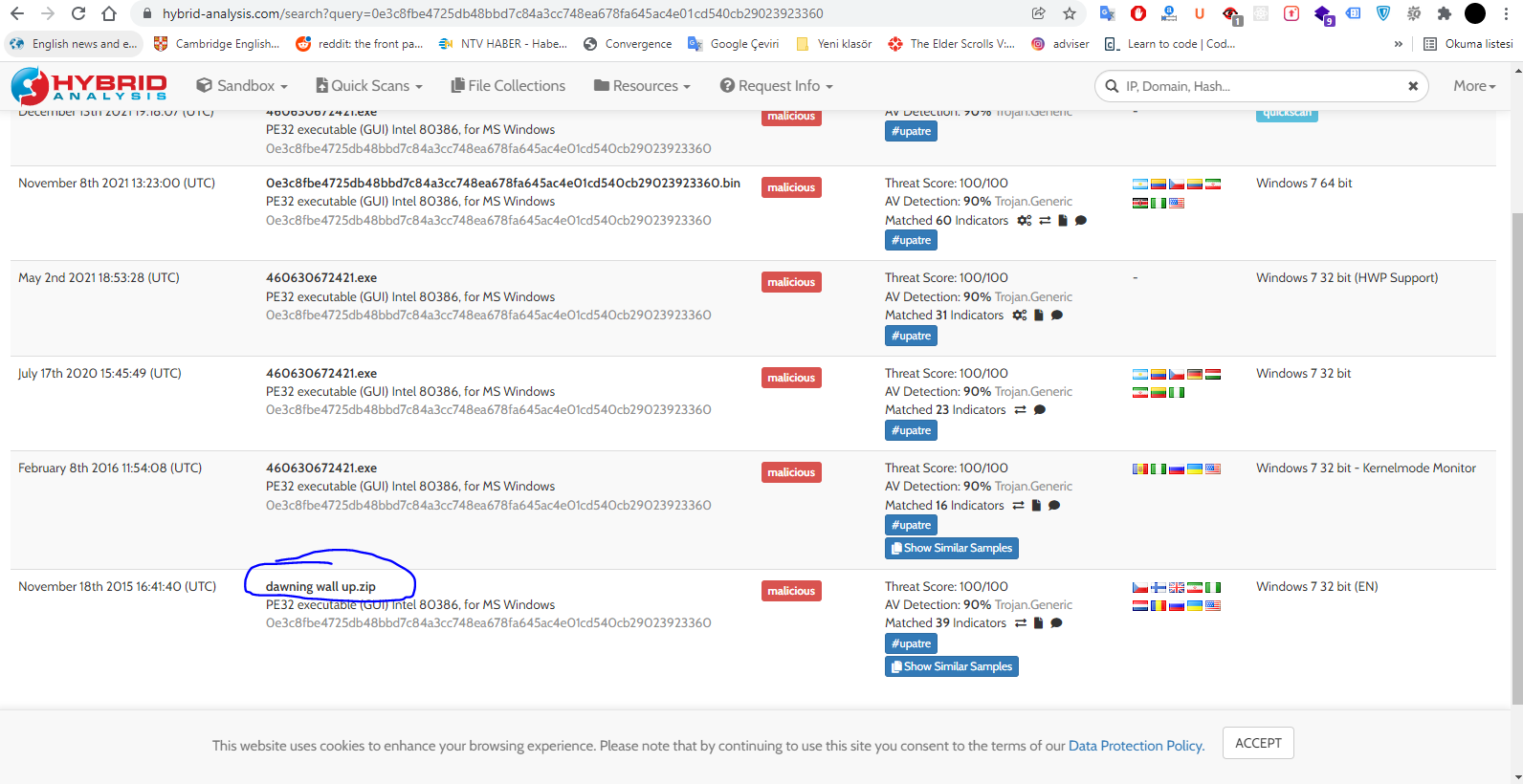
Free Automated Malware Analysis Service - powered by Falcon Sandbox - Viewing online file analysis results for 'https://hybrid-analysis .com/Part-RU/daa8547f1dbc8c994eed3725f3076aaf6c4e298b963fb712e53eb0fa2dc1e789'

Hybrid CPU/GPU/APU accelerated query, insert, update and erase operations in hash tables with string keys | Knowledge and Information Systems
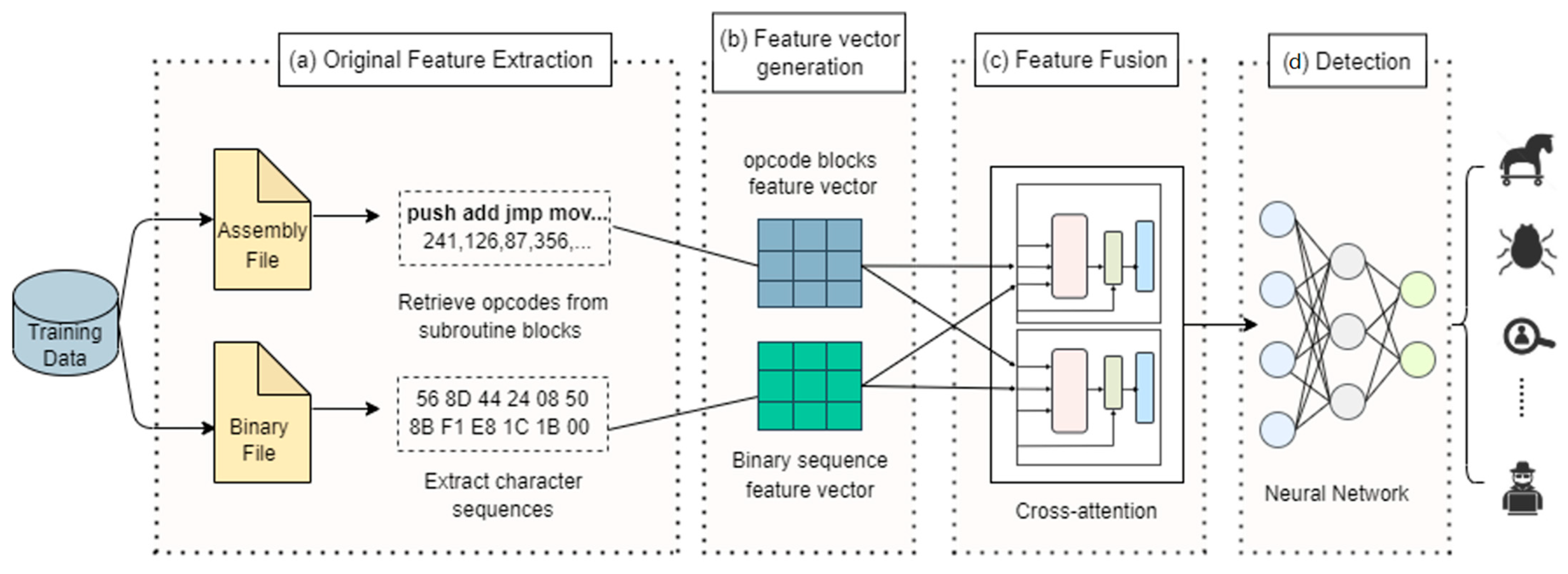
Electronics | Free Full-Text | A Hybrid Attention Network for Malware Detection Based on Multi-Feature Aligned and Fusion